Is Canada ready to protect its critical infrastructure?
Why cyber attacks on critical infrastructure are crucial in Canada today
The global digital landscape increasingly contains sophisticated and persistent cyber threats targeting critical infrastructure, and Canada is no exception. These threats can paralyze hospitals (CHUL, etc.), target electricity companies (Hydro Québec, etc.), infiltrate transportation networks (RTC, STM, etc.), and so on, leading to massive consequences such as:
- Service interruption
- Economic losses
- Privacy breaches
- Severity on human life
- Etc.
Canadian Trends and Statistics
In recent years, Canada has continued to make significant efforts in cybersecurity through a significant digital transformation:
–In 2022, the government introduced Bill C-26 (pending adoption), aimed at strengthening the resilience of IT systems in essential sectors: telecommunications, energy, transportation, finance, etc.
This project requires the designation and reporting of cybersecurity incidents and compliance with strict requirements.
- According to a credible source such as the CCC (Canadian Centre for Cybersecurity):
Between 2021 and 2024, we see a 23% increase in major incidents on critical infrastructure, and in 2023, more than 60% of hospitals and public service providers have experienced intrusion or ransomware attempts.
Given that the threat does not only come from cybercriminals and according to a National Threat Assessment report published in 2024, certain state actors are also a strategic threat to Canadian systems, namely: China, Russia, Iran and North Korea.
Risks, real cases, consequences
Several scenarios are available to us:
1- An attack on the electrical grid can critically compromise hospital operations
2- A breach in a municipal system can affect water or transportation servicesèche dans un système municipal peut affecter les services d’eau ou de transport
3- Etc.
Some concrete examples and consequences
We have some concrete cases:
1- Newfoundland and Labrador’s health system (2021): Paralyzed for weeks by a ransomware attack. We recorded deleted medical records, delayed treatments, and enormous costs
(https://ici.radio-canada.ca/nouvelle/1963328/groupe-hive-cyberattaque-2021-systeme-sante-terre-neuve-labrador)
2- Hydro-Québec (attempt in 2023): We noted an intrusion attempt by a state-affiliated group in 2023. Although thwarted, it highlighted significant vulnerabilities in the detection process (https://www.lapresse.ca/actualites/2023-04-13/cyberattaque/le-site-web-d-hydro-quebec-paralyse.php)
3- Toronto Pearson Airport (2024): This year we noted distributed denial of service (DDoS) attacks that temporarily disrupted ticketing systems and timetable displays.
These observed incidents show that no one is immune, and the attack surface continues to expand every day with digital expansion.
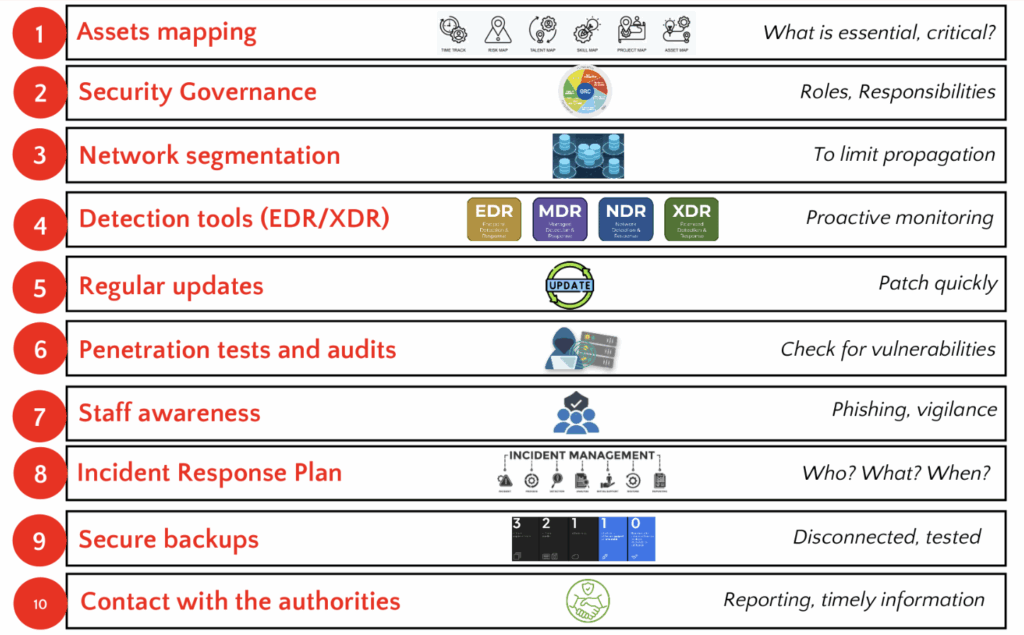
Key recommendations
For large infrastructures (example: energy, transport, hospitals, telecommunications, etc.):
- Establish a 24/7 security monitoring center (SOC 2 Type 2)
- Conduct regular cybersecurity audits based on industry standards such as ISO 27001, NIST, PCI-DSS, etc.
- Apply network segmentation to limit the spread of attacks
For SMEs or suppliers:
- Continuously raise staff awareness of social engineering risks (phishing, fraudulent calls, etc.)
- Implement accessible EDR/MDR solutions (for endpoint monitoring).
- Have a simple and structured incident response plan (tested at least once a year).
For the public sector:
- Collaborate closely with the CCC (Canadian Centre for Cybersecurity)
- Establish regional partnerships to share alerts and best practices
- Integrate cybersecurity into all digital transformation projects
Ultimately, it should be noted that preparation, resilience and responsiveness to potential attacks on critical infrastructure are not options but obligations for both government and private companies.
Measures for the protection of critical infrastructure